News & Events
Here you will find the latest news from our partners and the events we participate in.
Cubro Network Packet Broker EX48800
The Packetmaster EX48800 is a high-performance network packet broker designed to aggregate, replicate, filter, and load balance network traffic for security, monitoring and management tools.
Is Your Organization Ready for NIS 2?
This report is intended to guide your team in understanding the requirements, determining if you are within scope, and “update incident response plans and team set-ups in coordination with business continuity management (BCM) and the business.”
DVTEST Thermal RF Testing solutions
By combining RF isolated testing with thermal capabilities, DVTEST addresses the shortcomings of conventional separate test setups with their Thermal Shielded Enclosures.
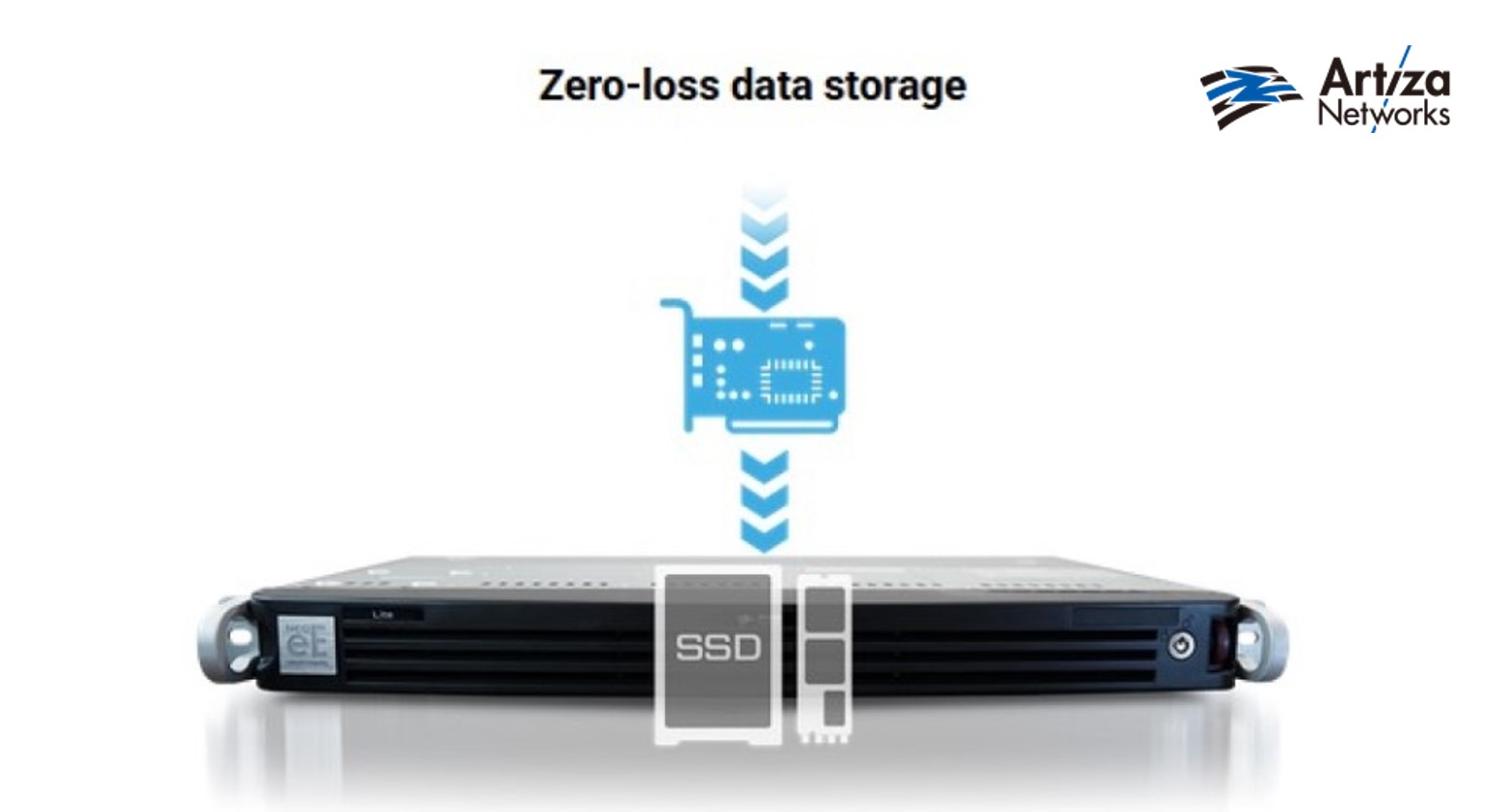
High-capacity packet capture
To secure the functionality of a network, effective monitoring of the data flow through it is required. etherExtractor makes securing backbone networks more reliable and efficient through high-capacity, lossless packet capture.
Maximizing Enterprise Cybersecurity Efficiency
By providing an independent layer of network visibility, Cubro gives enterprises greater control over their cybersecurity strategy, ensuring flexibility, scalability, and cost savings without compromising security.
Stop Apologizing: How to Transform Telecoms Customer Service
Recent insights confirm that customers prefer solutions over excuses, and this has major implications for telecom operators looking to improve their customer service.
Explore the E600 Medium-Sized Reverberation Chamber
Specially crafted for seamless integration, the E600 stands out for its robust capabilities and precision, enabling users to test wireless devices with remarkable accuracy.
Navigating Telecommunications Challenges in the Wireless Industry
Valid8 provides advanced diagnostic tools and software that capture and analyze data, providing detailed insights into operational efficiency of the system.
Strengthening Europe’s Digital Defence
The visibility solutions from Cubro can help defence sectors capture, filter, and analyse traffic in real-time to detect potential attacks or anomalies.
Latency: The Silent Killer of Digital Experiences
Latency is one of the critical factors that influence the user experience. Depending on the use case, even milliseconds of delay can significantly impact the performance of applications, from simple web browsing to complex real-time interactions.
Deep Dive into the I-Series Reverberation Chamber
The I-Series offers high-quality testing for smaller devices, while maintaining a reduced footprint, making it ideal for smaller labs. At the same time, it still delivers exceptional performance.
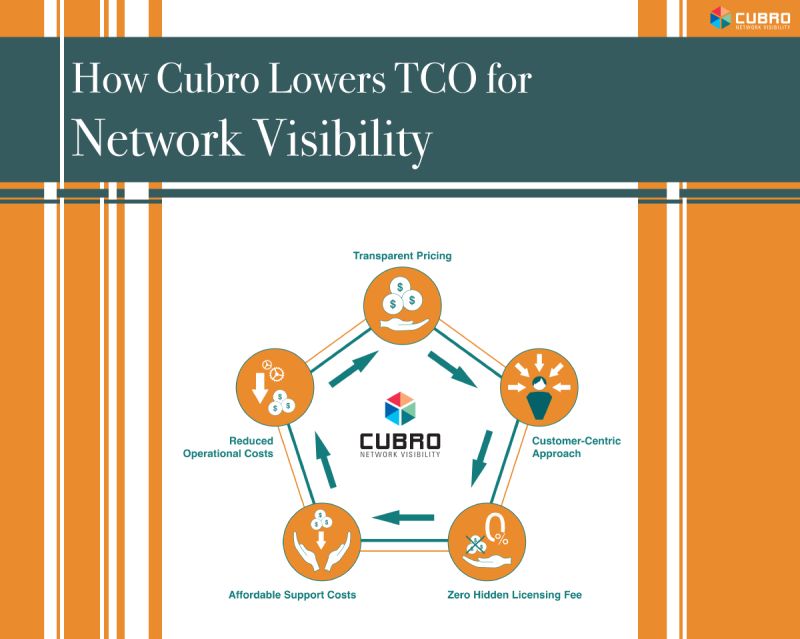
How Cubro lowers TCO for Network Visibility
When you choose Cubro, your organisation can significantly reduce the Total Cost of Ownership (TCO) while improving operational efficiency.
ThermaSAFE Thermal Test Enclosure
Thermal test enclosure, temperature range -80ºC to +225ºC, optional extended temperature range -100ºC to +300ºC.
Eutelsat OneWeb chooses Creanord to Power Next-Gen TWAMP Performance Hub
In the fast-evolving world of LEO satellite communications, network performance is everything.
Virtual Lab Testing Solutions
Virtual Labs enable a realistic, software-based network emulation of wireless, wireline & legacy network domains. With flexible subscription options available, Virtual Labs could be the right choice for your organization.
Introduction to Service Activation Testing for Data Transport Networks
By using a combination of RFC 2544, Y.1564, and iPerf3, network engineers can comprehensively evaluate the performance and reliability of their networks.
Advanced Network Packet Broker
The EXA32400 is a high-performance advanced network packet broker designed to optimize the flow of network traffic to security, monitoring, and management tools. This cutting-edge unit, part of the renowned Cubro G5+ series, brings unparalleled connectivity and flexibility to your network infrastructure.
3 ways AI is being used to make customer service more efficient and less frustrating
Within the context of customer service, delivering an effortless experience means providing easy-to-access support in a customer’s channel(s) of choice, removing the need to repeat information, reducing wait times and resolving customer problems faster.
Valid8 Telecom Network Cyber Security
Protecting telecommunications infrastructure from cyber-attacks is a complex and ongoing challenge, requiring a comprehensive understanding of the risks and the implementation of effective solutions.
Enhancing security in critical and industrial OT networks with tapping and aggregation solutions
Operational Technology (OT) encompasses the hardware and software systems vital for monitoring and controlling industrial processes.
The Future of AI in Telecom
Insights into how Subtonomy’s machine learning (ML)-driven platform is crucial in helping telecom operators manage customer support challenges and prevent churn.
Consumer User Experience Monitoring Use Cases
we will further look at a couple of critical consumer use cases: gaming and video streaming. This requires a seamless network to have an optimal user experience, and monitoring that goes beyond traditional network metrics.
Real-World Use Case: How Utel is making a difference
How a leading telecom provider managed to block more than 2 million fraudulent calls by leveraging the Utel Fraud Management System.
What have network TAPs ever done for us?
The fundamental component of any successful visibility solution is the 100% reliable, accurate source of network traffic delivered by network TAPs for performance and security monitoring.
Optimizing Internet User Experience through Active Monitoring
By implementing the right mix of technologies and best practices, you can significantly enhance the speed, reliability, and overall performance of your offered services and keep your customers happy and loyal.
Connecting the Dots of Observability
We now know that observability goes well beyond traditional network monitoring practices to take real-time visibility to the next level. It is worth taking a closer look at the ingredients needed to convert disparate data sources into actionable insights.
User Experience Monitoring in Modern Data Networks
Providing an excellent network experience to the users is key for operators today. Some studies on this topic show that the network is the top buying factor and the biggest contributor to churn.
User Equipment Testing Tools
Valid8's User Equipment Testing Solutions offer test operators a user friendly, comprehensive callbox platform to test devices for functional, conformance, security and performance.
Upgrade your Network Observability Toolkit
Leverage diverse data sources like flow, packet data and metrics to enhance your network observability. More tools don't always mean better data.
RFMaster™ SW for modeling the RF environment on wireless site types
RFMaster™ is Waterford's flagship software designed for modeling the RF environment on an unlimited range of wireless site types, enabling users to efficiently model, evaluate, and report with a simple, streamlined process.
Passive MIMO Measurement – Remote Mode
In the world of wireless communication, passive measurements play a crucial role in assessing channel characteristics, interference, and overall system performance.
Addressing Cybersecurity Challenges through Network, Device and Firewall Testing
Telecom has always been a prime target and network providers as well as device manufacturers need to be vigilant. The best way to ensure security and network response is to perform testing in a safe environment.
How to migrate mission-critical broadband to 4G and 5G networks
Want to migrate mission-critical broadband to 4G and 5G networks? Download the brochure from our partner Creanord.
Getting to the Heart of Observability
As monitoring gives way to observability, advanced medical devices can recognize specific heart conditions based on sound waves, electrical signals, and predefined patterns, with a boost from predictive analytics. This minimizes diagnosis time while expediting treatment.
Network TAPs – The First Line of Defense Against Cyber Attacks in Healthcare
This article explores the role of network TAPs in identifying and mitigating cyber threats and presents case studies where breaches could have been prevented.
Revolutionizing IVR: Making Interactive Voice Response User-Friendly
Interactive Voice Response (IVR) systems have long been a staple of telecom customer service, designed to streamline conversations and direct customers to the right departments. However, many users find IVR systems frustrating and impersonal.
Enhance Your AWS Security with Automated Audits
Secure your AWS environment with VIAVI advanced solutions for automated security group audits. Our white paper explores how CTEM can transform your network management, enhance IT efficiency, and simplify network complexity with our patented AI-learned EUE Scoring.
Testing Functional Aliases for Railway Communications
The rail industry, particularly in Europe, is looking to move away from the Global System for Mobile Communications-Railway (GSM-R) to Future Railway Mobile Communication System (FRMCS). Like many industries, the technologies currently in use are dated and will become obsolete relatively quickly.
Ebook: Streamlining Network Monitoring and SIEM Integration with Cubro Solutions
Network monitoring is the process of monitoring network traffic to identify issues, optimize network performance, and ensure network security. SIEM, on the other hand, is a security solution that combines security information management and security event management.
The Path to Mission Critical Broadband
Since private and land mobile radio technologies have limited data capabilities critical communication service providers are moving to 4G and 5G. This article is from our partner Creanord about mission-critical broadband - models, challenges, and solutions
The 4th Dimension of Threat Exposure Management
VIAVI Observer Sentry now features Traffic Insights, transforming how we understand and react to cyber threats. By analyzing traffic data, we uncover not just unwanted exposures but actual exploits, providing a whole new level of insight.
5 Ways to stop scam calls
Scam calls refer to fraudulent phone calls made with the intention of deceiving or defrauding individuals. Scammers typically pose as legitimate organizations, such as banks, government agencies, or well-known companies, in order to gain the trust of the recipient.
EMITE I70 Series Reverberation Chamber for OTA testing
Whether working with 5G networks, IoT devices, or examining coexistence scenarios, the I70 Series enables innovation while ensuring seamless connectivity and top-notch performance.
Can Interactive Voice Response become less of a pain?
Pretty much all large companies use it as a cost-effective way to deal with large volumes of queries, even though the research says that everyone seems to hate it. But that research can be somewhat misleading and automation can be the key to creating better personal interactions between the caller and customer service.
Creanord Launches Comprehensive Broadband Testing Solution
Creanord announced the launch of its state-of-the-art broadband testing tool designed to automate turn-up testing and troubleshooting of broadband internet services.
VIAVI State of the Network Study 2024/25
The 16th Edition State of the Network Study is leading this year’s trends to put network observability, tool consolidation, and Continuous Threat Exposure Management (CTEM) into focus.
Valid8 IMS Testing Solutions
Valid8 delivers a comprehensive set of testing tools for IP Multimedia Subsystems (IMS). We are helping our customers emulate end-to-end the IMS Client, CSCF, HSS and AS. With Valid8, our customers can test the AS or the Mobile Core.
Subtonomy accelerates expansion into Benelux and DACH via a new strategic partnership with Tucana
Subtonomy and Tucana are pleased to announce they have signed a new, exclusive partnership agreement covering the Benelux and DACH region, combining Subtonomy’s telecoms technical customer support suite and Tucana’s sales and delivery capabilities.
1 nano second timestamping for high-speed Network Packet Brokers
Cubro's flagship G5plus family of high-speed 100G Network Packet Brokers has been further enhanced. With the new software release, the EXA32100A/EXA64100 Network Packet Brokers allow adding 8-byte timestamp information to arriving packets.
When Precision, Clear & Guaranteed Communications Are A Requirement, Valid8 Responds
With the evolution of communication comes the need for more than voice in critical communication situations. Mission Critical Video and Data are growing in acceptance along with PTT.
The AI Opportunity in Security Operations
As a CISO, are you prepared for the benefits and risk of leveraging AI in security operations? As business leaders and decision makers embrace the potential of artificial intelligence (AI), they are confronted with critical questions.
Valid8 Completes DHS SBIR 23.1 Phase I MCX Technical Objectives
As part of the process, Valid8 became the first company to execute automated Mission Critical Push to Talk (MCPTT) Server-to-Server tests on a commercially available MCX Server.
Combat Fraud in Telecommunications
The Utel Fraud Management System tackles the challenges head-on, offering innovative anomaly detection solutions based on AI/ML to protect both telecom infrastructures and customers.
Advanced TWAMP Monitoring Techniques for 5G Networks
What if TWAMP protocol is your answer to advanced network monitoring? Refresh your knowledge of advanced TWAMP monitoring techniques for 5G networks.
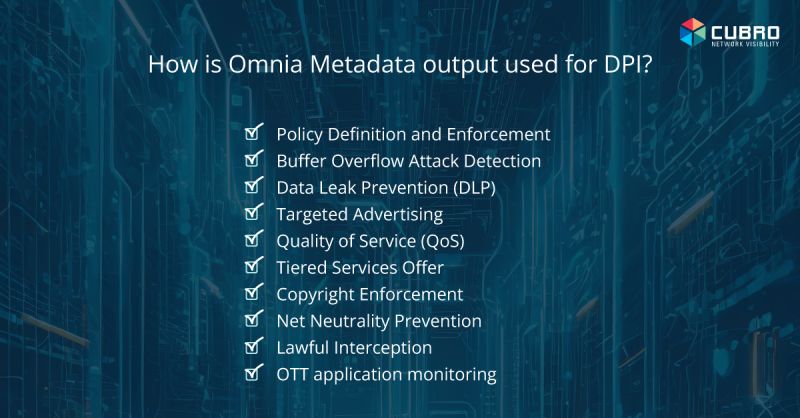
Cubro Omnia Solution Suite
With Omnics, operators can filter traffic based on user IP address, IMSI, and application detection, optimizing resource usage. DPI enables extracting relevant data, leading to lower volumes with essential information for advanced monitoring and analytics.
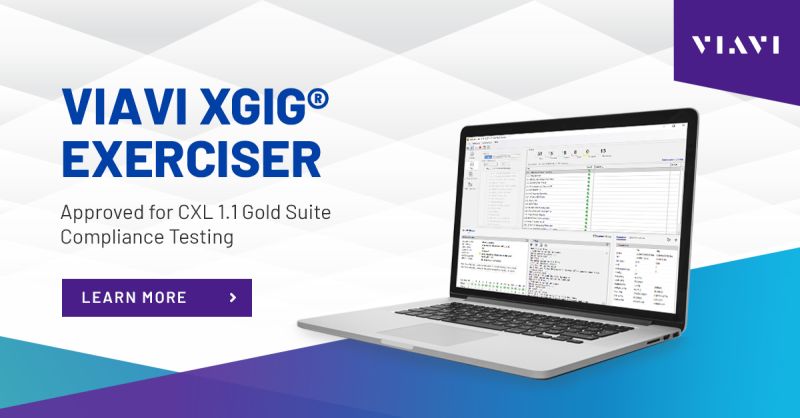
VIAVI Xgig Exerciser Approved for CXL 1.1 Gold Suite Compliance Testing
With this approval, the Xgig CXL Exerciser can now qualify CXL devices’ protocol implementations for the CXL Integrators List.
Creanord Introduces Network Health Check for 5G Transport Networks
Creanord is introducing a new Network Health Check for 5G transport networks that allows service providers to benchmark their mobile transport networks to make sure it is ready for 5G and provides an optimal end-user experience.
End-User Experience Monitoring
Understanding the user experience is the key to optimized application performance and issue resolution. End-User Experience Monitoring solutions from VIAVI utilize powerful machine learning to deliver real-time insights through a single, intuitive score.
Telecommunication fraud types explained
In the telco fraud territory we have many different fraud types. IRSF, subscription fraud, SIM-swapping, wangiri.. but what does it all mean, and more importantly, how does it affect your business and customers?
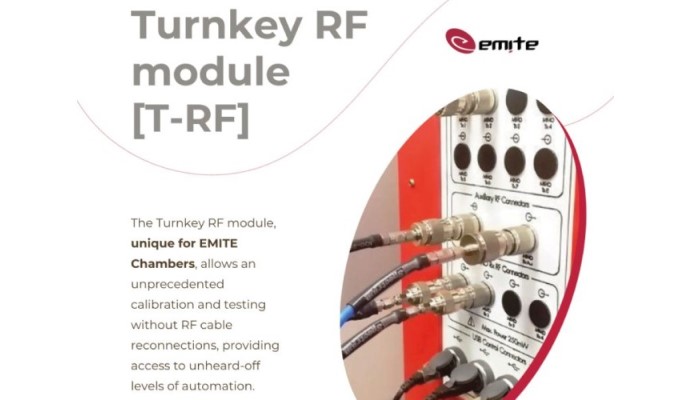
Discover the Revolution in Telecommunications Testing with EMITE Turnkey RF [T-RF] Module
This module enables unprecedented calibration and testing, eliminating the need for RF cable reconnections, facilitating never-before-seen levels of automation.
PCIe 6.0 Versatile 64GT/s PAM4 protocol testing platform
VIAVI PCIe6 protocol analysis solutions are capable of supporting 64GT/s data link speed operations with support for CXL and NVMe—as well as new PCIe6 specification features like PCIe FLIT Mode, FEC and TS0 Ordered Set.
New option for 64 Channel support for LoRaWAN testers
We would like to inform you about the newly released RWC5020B/M option for 64CH support from RedwoodComm.
5+1 Reasons why Vendor Independence is healthy for your business
Do you prefer an independent vendor for monitoring your network when it comes to signaling traffic? Here are 5 reasons why...
EMITE 5G OTA LAB: Leading the 5G Revolution!
EMITE's lab not only meets the most demanding standards but also contributes to the accelerated development of fully operative 5G OTA test systems, targeting carriers' real-world requirements and OEM capabilities.
VIAVI Network Monitoring Technology
Cybersecurity threats don’t just affect the safety of your enterprise; They can also be a major influence on a network’s performance. If your infrastructure isn’t secure, harmful actors may enter your network and target specific functions or devices.
Elevating Testing Standards with EMITE’s Hybrid Reverberation/Anechoic Chamber OTA Test Systems
EMITE’s Hybrid Chamber combines all the advantages of their revered Reverberation Chamber with the cutting-edge features of an Anechoic Chamber.
Creanord Completes First Cloud Connect Service Monitoring Project
Creanord has completed its first cloud connect service monitoring project providing business customers premium services with continuous monitoring and strict SLA guarantees at a large Tier 1 operator.
PCIe Test Challenges for Gen 4, 5 and 6
Detailed analysis of communication at all layers of the PCIe stack. Download your copy of this informative document here.
Omnishark – the Swiss army knife for network analytics & security
Omnishark can work as a troubleshooting tool or can be a source of metadata to an SIEM. For instance to offload the SIEM, because Omnishark can break down Giga and Terabit raw data into single events.
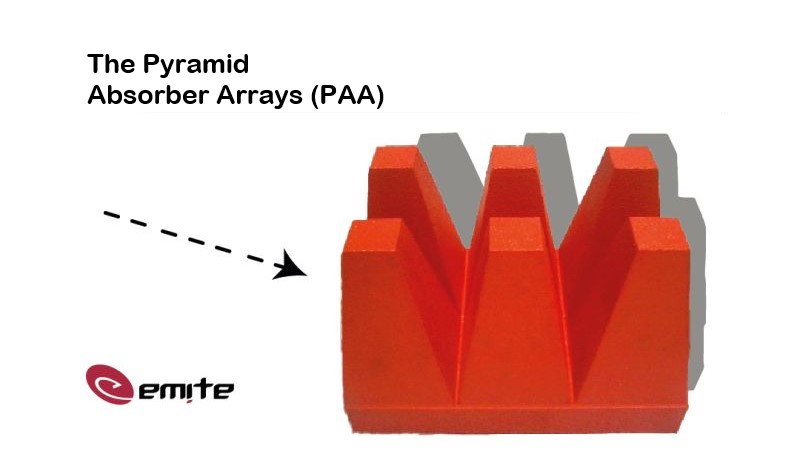
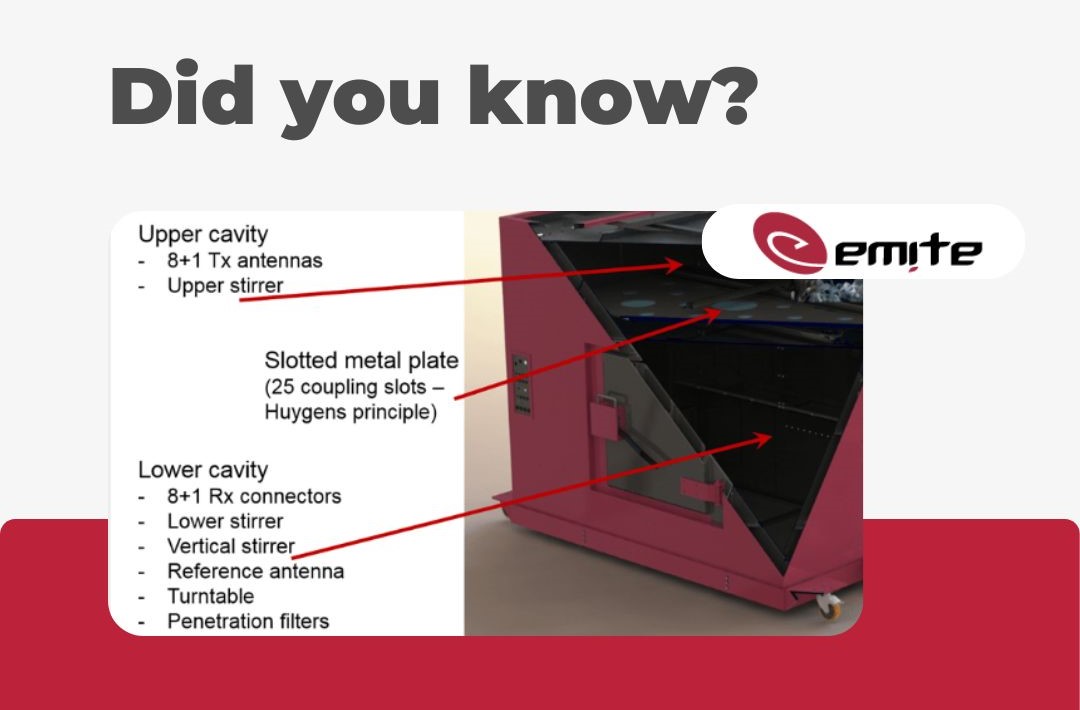
Transforming evidence with EMITE Pyramid Absorber Arrays
At the heart of their test chambers, you'll find EMITE's Pyramid Absorber Arrays (PAA), an essential tool for shaping the behaviour of the root mean square delay and coherence bandwidth in test scenarios.
Network Tapping of 2G through 5G Standalone telecom networks
This white paper provides an overview of physical and virtual network tapping and network packet broker network visibility solutions, their role in telecom networks and how they have evolved from 2G through to 5G Stand Alone network environments.
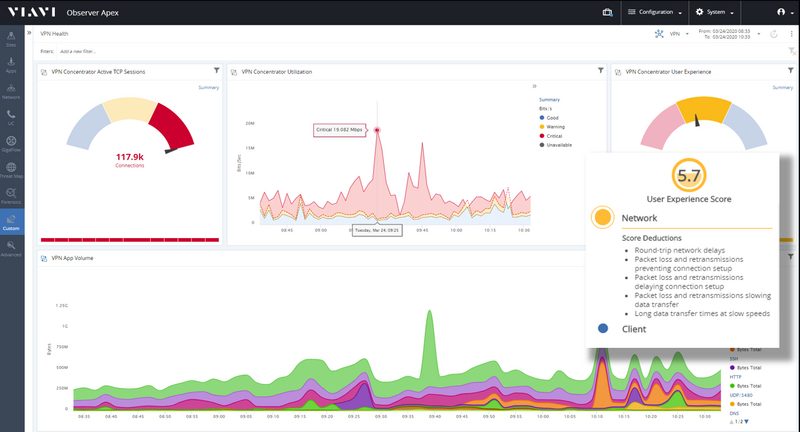
VPN Monitoring and Management
VPN oversubscription is a leading cause of network disruption for remotely based employees, severely impacting work productivity. The need to monitor VPN traffic and ensure that productivity is maintained has never been greater.
Discover Infinity with EMITE Phantoms
In the universe of telecommunications engineering, EMITE and SPEAG join forces to bring you an infinite range of Phantoms. Designed to simulate the electromagnetic properties of the human body, our Phantoms enable safe and efficient radiation testing.
PCIe 6.0 Protocol Analysis Testing Platform
The new VIAVI PCIe 6.0 protocol analysis testing platform will include Analyzers, Exercisers, and Interposers, provinding an option that enables its customers to capture 64 GT/s PCIe 6.0 traces on existing Xgig PCIe 5.0 equipment.
Using Digital Twins & Securing your 5G Network
we have 2 great EBooks for you! Learn how Valid8's digital twin capabilities can improve security, performance, and compliance testing. And also discover their current testing options and the value of a purpose-built, flexible and intuitive solution.
Reducing Power Consumption with Cubro’s Network Visibility Solutions
As more high-performance applications and cloud computing solutions come into play, the need for energy efficiency is increasingly important. Network visibility and monitoring is not an exception, as it consumes a significant amount of energy.
Find your perfect instruments and accessories with EMITE
Need high quality equipment? The range of instruments and accessories from our partner EMITE is second to none. From the most advanced test equipment to the simplest wrist phantom, they have it all.
End-User Experience Scoring
If you are challenged to quickly identify (and resolve) end-user network and application issues, now is the time for a new approach. Stop wading through unrelated KPIs and get the score on helping your users.
Digital Twin Emulation
By creating a highly realistic representation of real-world conditions, businesses can perform emulation, integration, testing, monitoring and maintenance before going live in production.
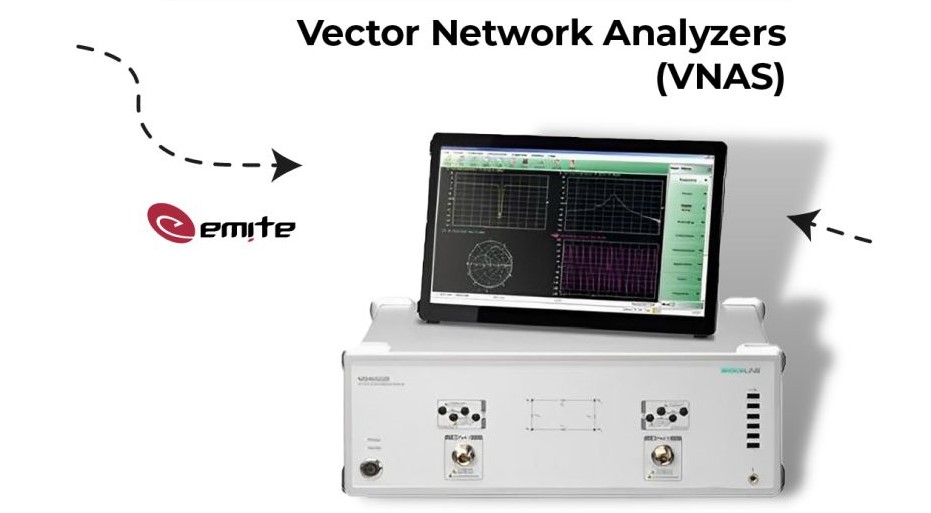
Optimise your Measurements with EMITE’s Vector Network Analysers
Our partner EMITE pre-selects optimal configurations for your OTA test needs, providing cost-effective VNA solutions for your calibration needs.
Cubro Visibility: Supporting Zero Trust Network Architectures
Companies are moving towards a zero-trust network architecture due to the frequency of target-based cyber attacks and increasing regulations for data protection and information security.
MIMO Measurements Made Simple: EMITE’s Patented Technology Inspired by Nature
Rather than simply focusing on the amount of light, our technology observes changes in the polarisation of light, allowing us to perform MIMO measurements with unprecedented accuracy and efficiency.
How 7 Companies Improved Network Visibility
As leadership demands greater accountability, IT teams are stepping up their network monitoring and management efforts to address these dynamic times and never-ending velocity of change.
3 Different test modes to suit your MIMO measurement needs
EMITE offers three different test modes to suit your MIMO measurement needs. Passive Mode Test. Active MIMO OTA Testing & Time Domain MIMO Tests.
Free Webinar – Pain Points and PCIe Protocol Analyzers
Join us for this webinar to learn more about megatrends for data-intensive applications and how the XGIG protocol analyzers family can support your product’s journey through the design, verification, compliance and optimization phases getting a faster time to market.
New distribution agreement with VIAVI
We are excited to inform you that we have entered into a distribution agreement with VIAVI Solutions Inc., a global leader in network test, monitoring, and assurance solutions. This agreement will enable us to offer you a wider range of high-performance products and services for your Compute, Storage and Transport (CST) and Network Performance and Threat Solutions (NPTS) needs.
Introducing Cubro’s Highly Advanced 400G Advanced Network Packet Broker EXA32400
Cubro is proud to unveil its groundbreaking 400G Advanced Network Packet Broker, featuring the most innovative P4 programmable chipset. Designed to address the evolving needs of high-speed networks, this cutting-edge NPB offers unmatched capabilities, flexibility and performance.
5 Ways to stop Wangiri fraud
Did you know that Wangiri is a Japanese term meaning "one ring and cut" and is one of the most serious telecom fraud types scamming millions of people each year? Check out how Utel is using machine learning to help combat these criminals.
Creanord Wins Large Shadow Router Replacement Deal
Creanord announced today that it has been chosen for yet another large shadow router replacement deal in order to improve scalability, granularity, and accuracy for core network performance monitoring at a large Tier 1 operator.
Large size Reverberation/Anechoic Chamber 200 MHz to 220 GHz
The F-Series are ideal for testing devices and antennas over a wide frequency range, from 200 MHz to 220 GHz, covering all 4G, 5G and 6G communication bands. Designed to provide fast and accurate test solutions, these state-of-the-art anechoic chambers deliver optimal results in OTA (Over-the-Air), MIMO and Massive MIMO testing.
LockBit for Mac | How Real is the Risk of macOS Ransomware?
In this post we explore both the details of the LockBit sample uncovered and the larger question of how real is the risk of ransomware on macOS endpoints.
5G Security
Security is a wide topic and has different angles to it, for example, ITU-T has defined eight security dimensions shown in the table below. While these are important factors, this blog focuses more on the 5G network security measures and attempts to bring how to utilize data regardless of regulation and tight security in the summary section.
New features in the field of Targeted Attack Protection
With the introduction of 4 new features in the field of Targeted Attack Protection, Proofpoint is even better prepared for malicious content than ever before!
Tiny but unique Reverberation Chamber
We present the small-sized reverberation chamber I60 from our partner Emite. An OTA (Over-the-Air) test chamber with a unique price-performance ratio and user friendly.
Utel Open RAN Monitoring: Troubleshooting 5G Fronthaul and multi-vendor solutions
Open RAN networks are already becoming increasingly popular due to the range of advantages they deliver, but the transition to Open RAN is not straightforward.
Telecom Industry’s Highest Performing TWAMP Reflector for End-to-End 5G Performance Management
The TWAMP protocol was around for a while and has become the de facto standard for measuring end-to-end performance in mobile and fixed networks. Two-way active measurements are essential for detailed visibility of end-to-end performance in 5G networks.
The most advanced Reverberation Chamber on the market
The E-Series can perform single measurements, batch tests, protocols or campaign tests for different frequency bands, different technologies and different channel models, operating overnight without human intervention.
Simplified Email Authentication through Hosted SPF and DKIM Services
Email authentication is a critical measure to help prevent threat actors from sending email under the pretense of being from your organization. This tactic is referred to as domain spoofing and, if left unprotected, allows cyber criminals to weaponize your sending domains for malicious cyber attacks.
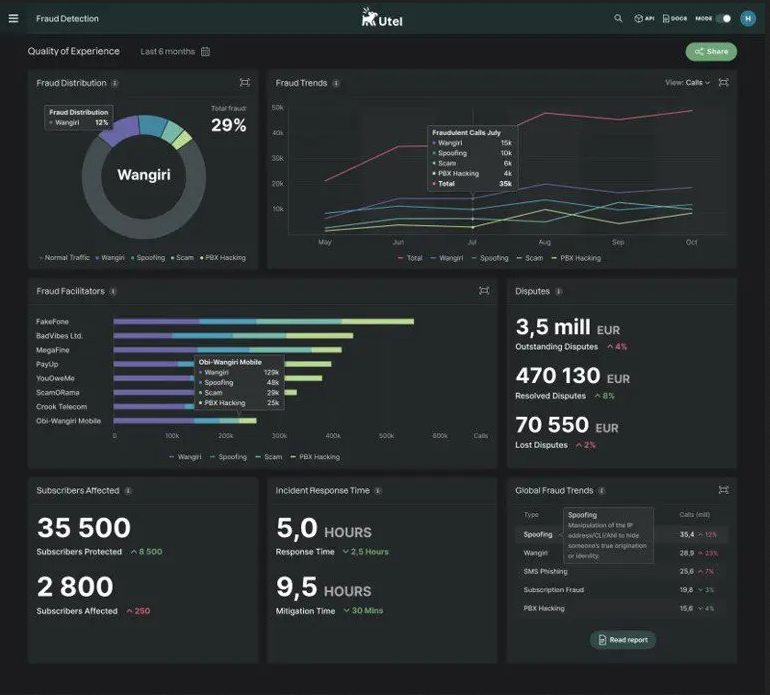
New fraud detection dashboard Utel
Check out this short video snippet of the new fraud detection dashboard from our partner Utel! They have been hard at work on some nice front-end bells and whistles lately, as they are getting closer to launching this new tool full-scale.
Chatbot Phishing Emails: What You Need to Know
You may have heard about a new chatbot technology, ChatGPT, that uses recent advances in artificial intelligence (AI) to create human-like conversations. As ChatGPT is free and available for widespread use, cybersecurity experts are looking at the risks of ChatGPT-generated phishing emails.
Get Confidence on the 5G Network Quality
Seeking better confidence in the mobile network quality? Read how the world’s most advanced 5G service providers did it in this customer case.
Proofpoint Signs Definitive Agreement to Acquire Illusive
SUNNYVALE, Calif., December 12, 2022 – Proofpoint Inc., a leading cybersecurity and compliance company, today announced it has entered into a definitive agreement to acquire Illusive, a leader and pioneer in Identity Threat Detection and Response (ITDR). The acquisition is expected to close by January 2023, subject to customary closing conditions. With this acquisition, Proofpoint [...]
5 Cyber Scams to Watch Out for This Holiday Season
As inboxes flood with messages about markdowns galore, opportunistic cyber criminals use this time to step up their holiday scams. This blog covers why seasonal retail is under attack by cyber criminals and what businesses and shoppers can do to keep up their cyber defenses.
The Humble Packet – Powerful Content for Threat Detection and Response
Deep packet inspection (DPI) provides the sum of all knowledge from the network. Although deriving meaningful insights from packets is difficult, those insights help companies create an indelible line of defense for the network.
Proofpoint Recognized in 2022 Gartner® Market Guide for Data Loss Prevention
In today’s world, your DLP solution must provide visibility across multiple channels of data loss—but not require multiple teams to manage it. It must scale with your company’s information protection needs while protecting data without interruption. And since data doesn’t lose itself, your DLP solution must be people-centric, providing insight into user behavior.
Rise in Identity-Based Attacks Drives Demand for a New Security Approach
The frequency of ransomware attacks has doubled over the last couple of years, accounting for 10% of all breaches. The ‘human element’ is the primary means of initial access in 82% of breaches.
How to stay safe online this holiday season
Cybercriminals always follow the money, and as online shopping ramps up, it’s vital that you protect yourself and your data from becoming compromised. Click through for tips from our partner Proofpoint on how to stay safe online this holiday season.
Benefits of Packet-Level Data
This Omdia survey looks at how both network and security teams use packet-based data; those managing networks are often focused on reliability and performance; those in security teams are looking for how best to apply controls to manage risk, how to know when attacks occur, and what actions to take in mitigation.
Deep Packet Inspection Technology
Deep Packet Inspection (DPI) is an advanced method of examining and managing network traffic. The inspection allows software/hardware to access, analyse and modify payload (data) portions of network packets.
Base Station OTA overnight testing in Anechoic Chamber using MIMO Analyzer GUI Software
Watch this video showing how to measure Base Station OTA Key Performance Indicators (KPI) such as Radiated Transmit Power (RTP), Base Station Output Power (BSOP) and Transmitter Spurious Emissions (TSE).
On the Board of Directors? Beware of These Six Common Cyber Security Myths
In this blog we cut through the clutter and cover the basics of cyber risk management for directors by dispelling six common cybersecurity myths.
Introducing Network Compliance as a Service
Can you easily find and fix issues that impact the stability and security of your network? Instead of selling you a tool, we bundle our platform with implementation services and a proven methodology that simply delivers results.
New Digital Radio Testers Launch
The Digital Radio Tester RWC2010C supports the DAB, DAB+, DMB, DRM30, DRM+, AM, FM and RDS system.
Informatiebescherming- Het perspectief van binnenuit
Kijk hoe beslissers in Nederland het hoofd bieden aan CyberSecurity-risico's van binnenuit. Download het rapport aan en ontdek de beste manieren om uw gegevens te beschermen.
Considering the impact of IoT on your network traffic
What’s likely to be the impact of IoT on network traffic and what do you need to be aware of as you take it into account?
Network Tapping of 2G through 5G Standalone telecom networks 2022
This white paper provides an overview of physical and virtual network tapping and network packet broker network visibility solutions, their role in telecom networks and how they have evolved from 2G through to 5G Stand Alone network environments.
5G Security Suite
The Valid8 Security Test Suites are suitable for auditing security of 5G network nodes including UE, gNodeB, AMF, SMF, UPF, according to standards including NESAS, 3GPP.
A Crash Course on Security Analytics — And How to Spot Fake UEBA From a Mile Away
CISOs interested in having a better understanding of security analytics, such as Machine Learning (ML) or User and Entity Behavior Analytics (UEBA), have limited — or shall we say poor — sources of information.
Email Rapid Risk Assessment
With a free Proofpoint Email Rapid Risk Assessment, you get a comprehensive view of your risk posture across your email infrastructure. We give you the controls you need to protect your organization from the evolving threat landscape, including ransomware, credential phishing and email fraud.
Blog – Complex SLA’s Require Proper Monitoring
PULScore SLA Dashboard Due to evolving networks and the increased complexity of the networks caused by the introduction of virtualization, cloud computing, 5G distributed architectures and the like, the outages in the networks are increasing.
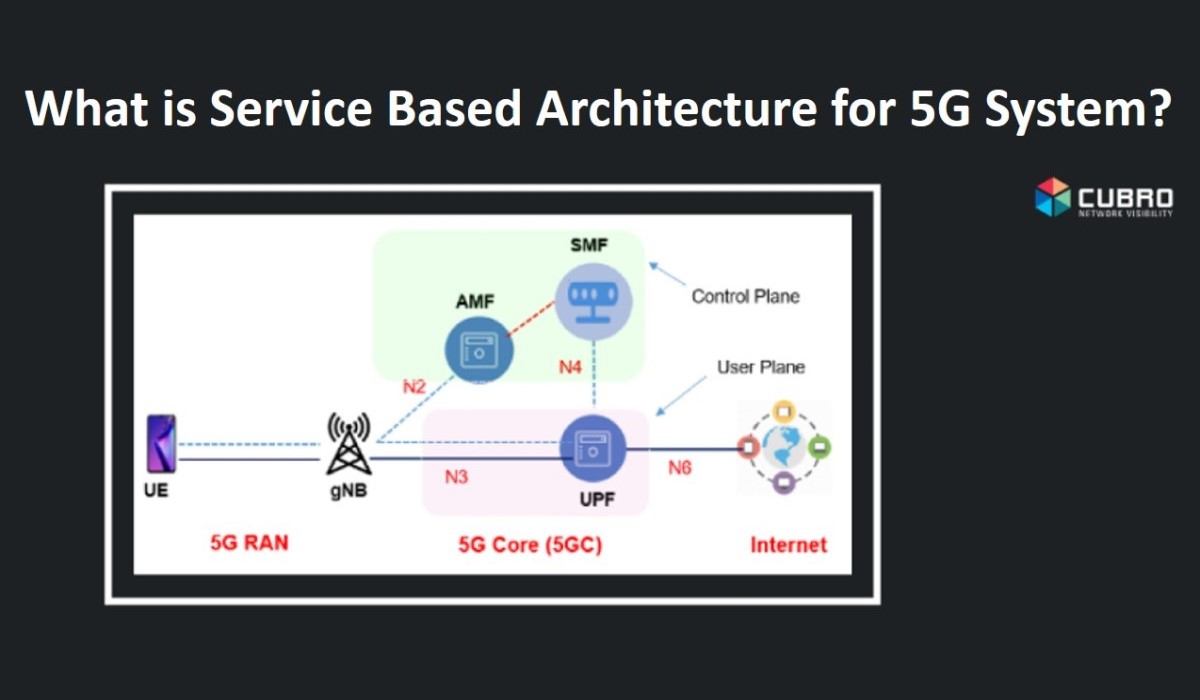
Blog – What is Service Based Architecture for 5G System
A 5G System (5GS) consists of User Equipment (UE), 5G Base station (gNB), 5G and a 5G Core Network (5GC). In 5GS architecture, the 5GC is located at heart and enables the 5G RAN to support 3GPP defined three use cases.
Blog – The CISO’s Response Plan After a Breach
There’s no escaping the fact that post-breach leadership is a part of every security team member’s job. Spearheading post-breach action and recovery is the ultimate test of a security leader’s skills, confidence, and mettle.
Blog by Creanord – A Successful Journey to 4G/5G-based Mission-Critical Mobile Broadband
Migration of mission critical broadband networks is long overdue. TETRA networks have served the critical communication community well, but they no longer support today’s demands for high capacity broadband services.
Utel Voice Recording and Playback: A proven solution for SIP/RTP networks & customer care
Delivering consistent Quality of Experience (QoE) for VoIP and VoLTE customers in packet-switched networks is a challenge for many operators. If Quality of Service (QoS) is not delivered consistently for voice calls, poor QoE can result.
Blog – Top 10 Ways to Protect Your Active Directory
Active Directory (AD) is a high-value target for attackers, who frequently attempt to compromise it to escalate their privileges and expand their access. Unfortunately, its operational necessity means that AD must be easily accessible to users throughout the enterprise
NETSCOUT’s Omnis Security Platform
Proactively block threats before they become attacks. The only cybersecurity platform that provides end-through-end visibility at lightning speed.
Introducing the RF shielding enclosure
Introducing the RF shielding enclosure from our partner RedwoodComm that guarantees 100 dB isolation over a wide range of frequency bands, up to 6.5GHz.
Joint Emite and Anritsu solution adds 6 GHz band to test latest Wi-Fi 6E devices
EMITE and Anritsu Corporation have added the 6 GHz band to their newly integrated testing system, allowing testing to the new IEEE 802.11ax WLAN standard. The new band adds to the already available 2.4 GHz and 5 GHz bands.
New highly portable and affordable LoRa tester
An RWC5021P from our partner RedwoodComm will let you check the function of your LoRaWAN devices no matter where you are, without taking up a lot of room on your desk.